DNS - Domain Name System
This section will cover ways to enumerate Domain Name System (DNS).
Table of Contents
- Overview
- Default Configuration
- Dangerous Settings
- Enumerating DNS
- dig
- Gobuster
- dnsenum
Overview
Domain Name System (DNS) is used to resolved human readable names to IP addresses. An example will be where the domain gohspace.com will have a DNS entry pointing to the IP address of 192.168.1.200.
There are several types of DNS servers:
- DNS root server
- Authoritative name server
- Non-authoritative name server
- Caching server
- Forwarding server
- Resolver
The below table will list the type of DNS server and their description:
| DNS Server Type | Description |
|---|---|
| DNS Root Server | The root servers are responsible for the top-level domains (TLD). As the last instance, they are only requested of the name server does not respond. |
| Authoritative Name Server | These servers hold authority for a particular zone. They only answer queries for their area of responsibility, and their information is binding. If the authoritative name server cannot answer a client's query, the root name server will take over. |
| Non-authoritative Name Server | These servers are not responsible for a particular DNS zone. Instead, they collect information on specific DNS zones themselves, which is done using recursive or iterative DNS querying. |
| Caching Server | The caching server cache information from other name servers for a specific period. The authoritative name server determines the duration of the storage (cache TTL). |
| Forwarding Server | Forwarding servers perform only one function; forward DNS queries to another server. |
| Resolver | Resolvers are not authoritative DNS servers but perform name resolution locally in the computer or router. |
The below image will show the hierarchy for domains.
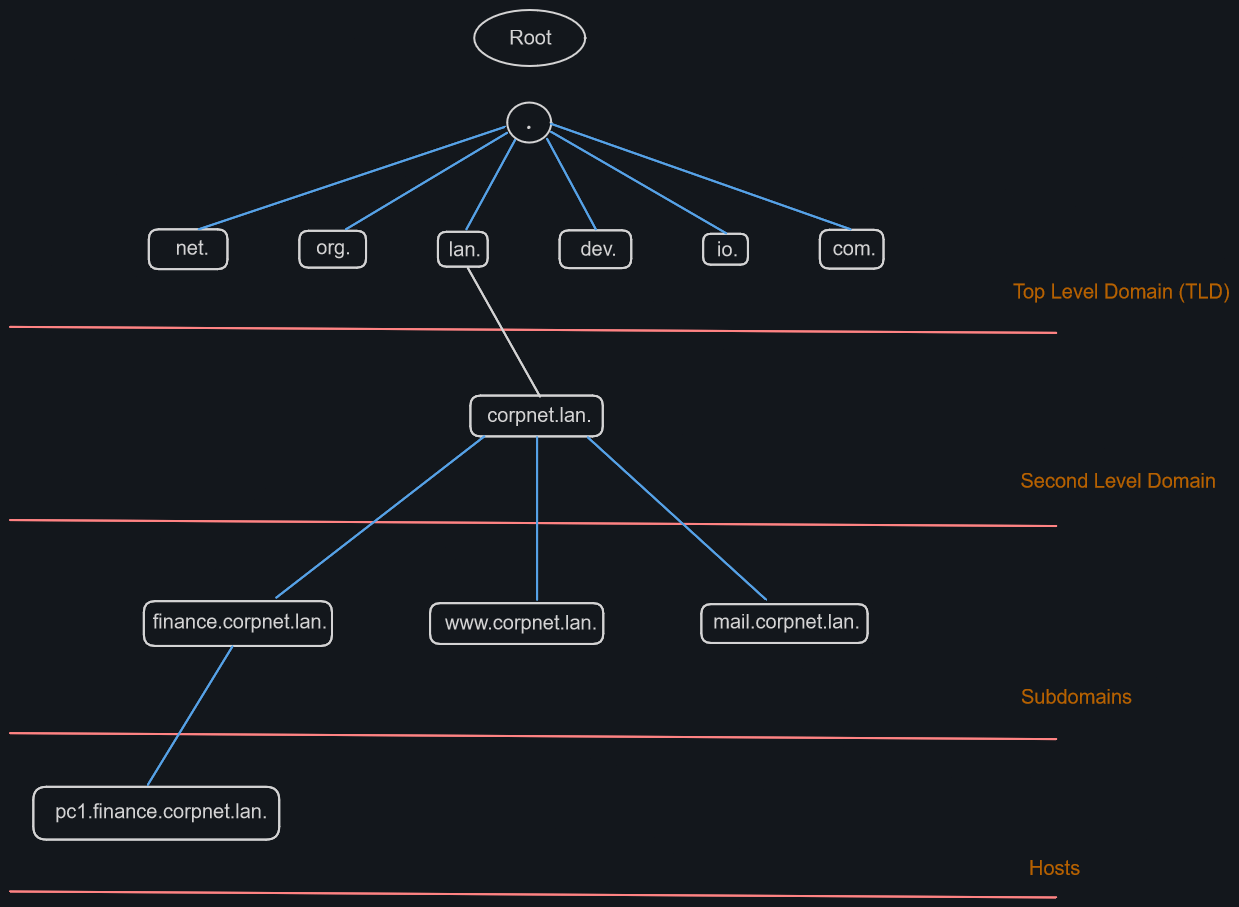
DNS is mainly unencrypted. This allows a third-party to sniff the traffic and view what sites you are visiting for example.
There are solutions for encrypting DNS. Some examples of such are:
- DNS over TLS (DoT)
- DNS over HTTPS (DoH)
- DNSCrypt
DNS also stores other information and outputs additional information about the services associated with a domain.
There are also different DNS records that serves different purposes. The below table will list some of them.
| DNS Record | Description |
|---|---|
| A | Returns an IPv4 address of the requested domain. |
| AAAA | Returns an IPv6 address of the requested domain. |
| MX | Returns the mail servers. |
| NS | Returns the DNS servers (name servers) of the domain. |
| TXT | This record can contain various information. It is a "all-rounder" that can be used such as validating Google Search Console or used for SPF and DMARC entries to validate mail traffic to protect it from spam. |
| CNAME | This record acts as an alias. If a domain has the same IP address with a subdomain, we can create an A record for the main domain and CNAME record for any subdomains under it. |
| PTR | Returns the domain name of an IP address (acts as a reverse lookup). |
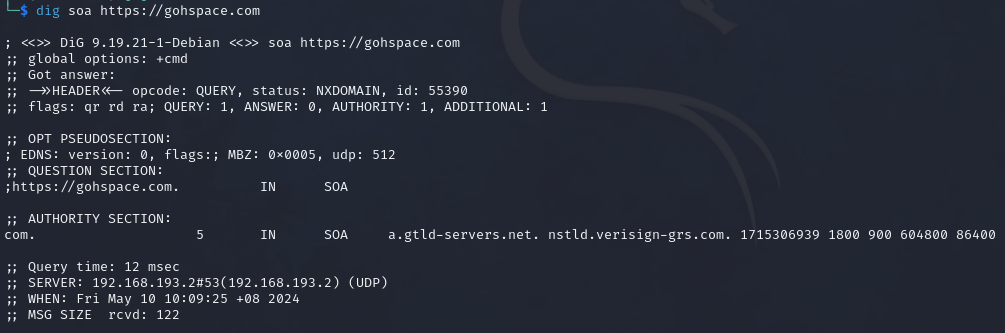
| SOA | Provides information about the corresponding DNS zones and email address of the administrative contact. |
The SOA record is located in a domain's zone file and it specifies who is responsible for the operation of the domain and how DNS information for the domain is managed.
Default Configuration
There are many different types of configurations and settings for DNS. This part will only focus on three different ones:
- local DNS configuration files
- zone files
- reverse name resolution files
On Linux, the DNS server is often Bind9. Its local configuration file (named.conf) is roughly divided into two sections. Firstly, the options section for general settings. Secondly, the zone entries for the individual domains.
The local configuration files are usually:
- named.conf.local
- named.conf.options
- named.conf.log
The named.conf is divided into several options that controls the behaviour of the name server. A distinction is made between global options and zone options.
Global options are general and affect all zone. A zone option only affects the zone to which it is assigned. Options not listed in named.conf have default values. If an option is both global and zone specific, then the zone option takes precedence.
Dangerous Settings
There are many ways that DNS can be attacked. The below table will list some settings that can be dangerous.
| Option | Description |
|---|---|
| allow-query | Defines which hosts are allowed to send requests to the DNS server. |
| allow-recursion | Defines which hosts are allowed to spend recursive requests to the DNS server. |
| allow-transfer | Defines which hosts are allowed to receive zone transfers from the DNS server. |
| zone-statistics | Collect statistical data of zones. |
Enumerating DNS
Some tools that we can use are:
- dig
- gobuster
- dnsenum
Dig
We can use the tool called dig in order to make DNS queries to gather information about our target. There are many queries we can perform using dig.
Some common ones are:
- NS Query
- Version Query
- ANY Query
- Zone Transfers
NS Query
We can find out which other name servers it knows by using the @ symbol in our command.
dig ns gohspace.com @8.8.8.8
Command breakdown:
ns- Specify to perform a NS query.gohspace.com- Specify the domain name.@8.8.8.8- Specify the IP address of the DNS server.
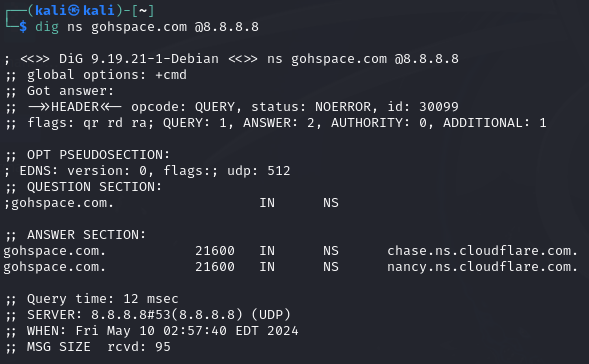
We can see that there are two name servers being used from the above screenshot.
Version Query
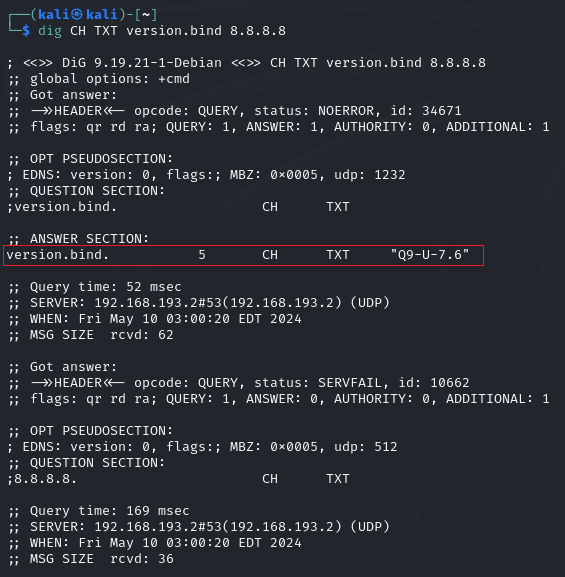
Sometimes it is possible to query a DNS server's version using a class CHAOS query and type TXT. However, the entry must exist for it to work.
dig CH TXT version.bind 8.8.8.8
Command breakdown:
CH- Specify to use a CHAOS query.TXT- Specify the type to be TXT.version.bind- Specify to get the version of the server.8.8.8.8- Specify the IP address of the DNS server.
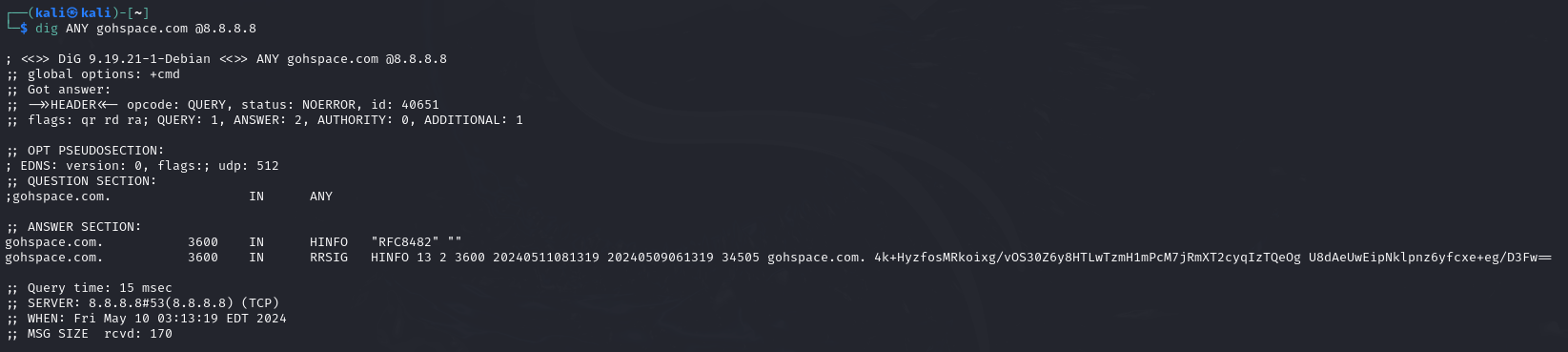
ANY Query
We can use the ANY option to view all available records. This will get the server to show us all available entries that it is willing to disclose. It is important to note that not all entries from the zones will be shown.
dig any gohspace.com @8.8.8.8
Command breakdown:
any- Specify to use the ANY query.gohspace.com- Specify the domain name.@8.8.8.8- Specify the IP address of the DNS server.
Zone Transfer
Zone transfer refers to the transfer of zones to another DNS server. This process usually happens over TCP port 53. This process is abbreviated to Asynchronous Full Transfer Zone (AXFR). Since a DNS failure will have severe consequences, the zone file is almost invariably kept identical on several name servers.
We can use the following command to check if we can perform a zone transfer.
dig axfr mydomain.lan @10.10.10.1
Command breakdown:
axfr- Specify to perform a DNS zone transfer.mydomain.lan- Specify the domain name.@10.10.10.1- Specify the IP address of the DNS server.
If an administrator used a subnet for the allow-transfer option for testing purposes or a workaround solution or set it to any, everyone will would query the entire zone file at the DNS server. In addition, other zones can be queried which can lead to the disclosure of internal IP addresses and hostnames.
dig axfr internal.mydomain.lan @10.10.10.1
Gobuster
The individual A records can with the hostnames can be found using brute-force attacks. To do this, we will need to a wordlist. A good example will be using SecLists.
We can use GoBuster and the following command to perform the brute-force attack.
gobuster dns -d gohspace.com -w ~/main/wordlists/SecLists/Discovery/DNS/namelist.txt
Command breakdown:
dns- Specify to use the DNS module.-d gohspace.com- Specify the domain name.-w ~/main/wordlists/SecLists/Discovery/DNS/namelist.txt- Specify the wordlist to use.
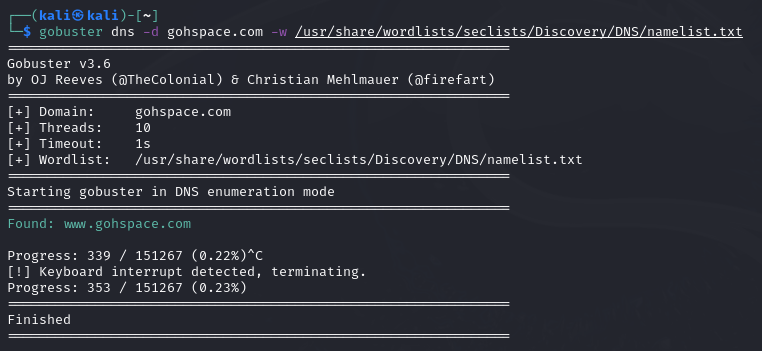
From the above result, we can see that there is a subdomain called www.gohspace.com.
dnsenum
We can also use dnsenum to enumerate for subdomains. We can use the following command:
dnsenum --dnsserver 8.8.8.8 --enum -p 0 -s 0 -o subdomains.txt -f ~/main/wordlists/SecLists/DNS/namelist.txt gohspace.com
Command breakdown:
--dnsserver 8.8.8.8- Specify the IP address of the DNS server.--enum- Specify to enumerate DNS records.-p 0- Specify how many packets to send per second.-s 0- Specify how long to wait between whois queries.-f ~/main/wordlists/SecLists/DNS/namelist.txt- Specify the wordlist to use.gohspace.com- Specify the domain to enumerate.